Abusing Promo Code Signup Flows for Reliable Discounts with Major Retailers
On the contemporary internet, high-fidelity tracking of customers is of paramount importance for retailers. Instead of generating trace data markers like browser fingerprints and cookies, having a customer directly create an account with a retailer allows for unambiguous tracking of their purchase behavior. This feeds downstream systems that recommend future products and increase revenue per customer over time.
In exchange for signing up, most retailers provide generous first-time signup benefits to their would-be user-customers. However, retailers are purveyors of physical goods first, and savvy engineering operations second. In many cases, retailers systemically cut corners when developing their user signup flows. Crucially, these development teams also cut corners when provisioning first-time promo signup codes.
Promo code abuse is somewhere between a $300 million to $600 million business. Finding ways to scale the provisioning and sale of coupons is, thus, a huge target for botmakers. Often, the user flow for a promo code signup is as follows - a user visits the retailer’s site, is enticed to sign up via overlay, on-page element, or at the point of checkout, and then provides their email address in order to receive the promo code via e-mail. Then, an email will arrive with the promo code embedded, which can then be inserted into any checkout flow to apply the discount.
In every case, the promo code that is provisioned to the user is, importantly, provisioned to that specific email address. In theory, locking the promo code to accounts that are logged in, and verified with, that email address would significantly reduce the ability to abuse the promo code provisioning process. In practice, no such measures are taken on many prominent retailer sites.
Consider the following - a technically inclined individual wants to make some money on the side - they also identify this weakness. Using a proxy network and standard selenium automation tools, they can create automation flows against retailers of choice to create repeatable processes for “mining” promo codes. They could then sell these on forums to individuals, or to other folks looking to resell the promo codes. All the while, by employing proxy networks and some simple methods of obfuscation, they can remain effectively undetectable from these retailers. As soon as one retailer identifies the weakness, the developer could simply close up shop and move to the next, as this is such a systemic problem.
Look at all those clearly tailored SEO links ready to give us promo codes!
In fact, promo code identification is one of the more abused SEO terms on the internet. Companies like Rakuten, RetailMeNot, and so forth even built an industry out of identifying and provisioning promo codes to users through less shady means.
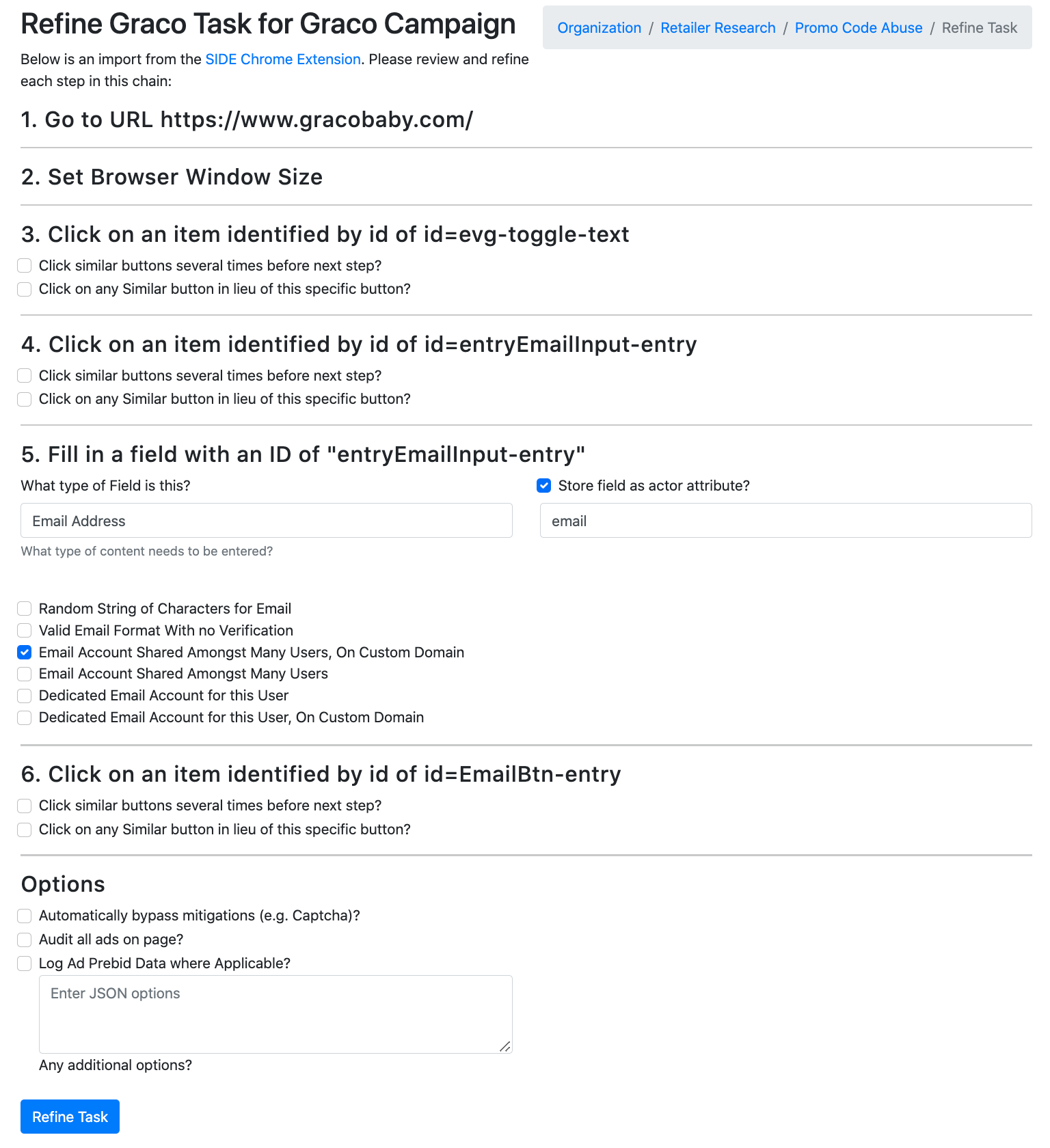
But how much money would it cost for an attacker to automate these promo code generations? Practically speaking, how economically feasible would such a grey-market abuse pattern be? With IPM’s Vulnerability Engine, we are able to generate automations that directly test and measure these abuse patterns, and determine the minimum viable cost of abuse. Consider Graco Baby, a company that sells consumer goods for new parents and people purchasing gifts for those new parents. Graco provides a 15% first-time signup bonus. Using the Vulnerability Engine we can record an automation that generates these dynamically, provisioning anonymous email addresses that we can send and receive emails from in order to receive these promo codes, and then, store them and extract them programmatically. First, we set up our automation in the vulnerability engine by uploading a JSON manifest explaining to the VE what the job will be:
A screenshot of the IPM vulnerability engine's automation creation flow
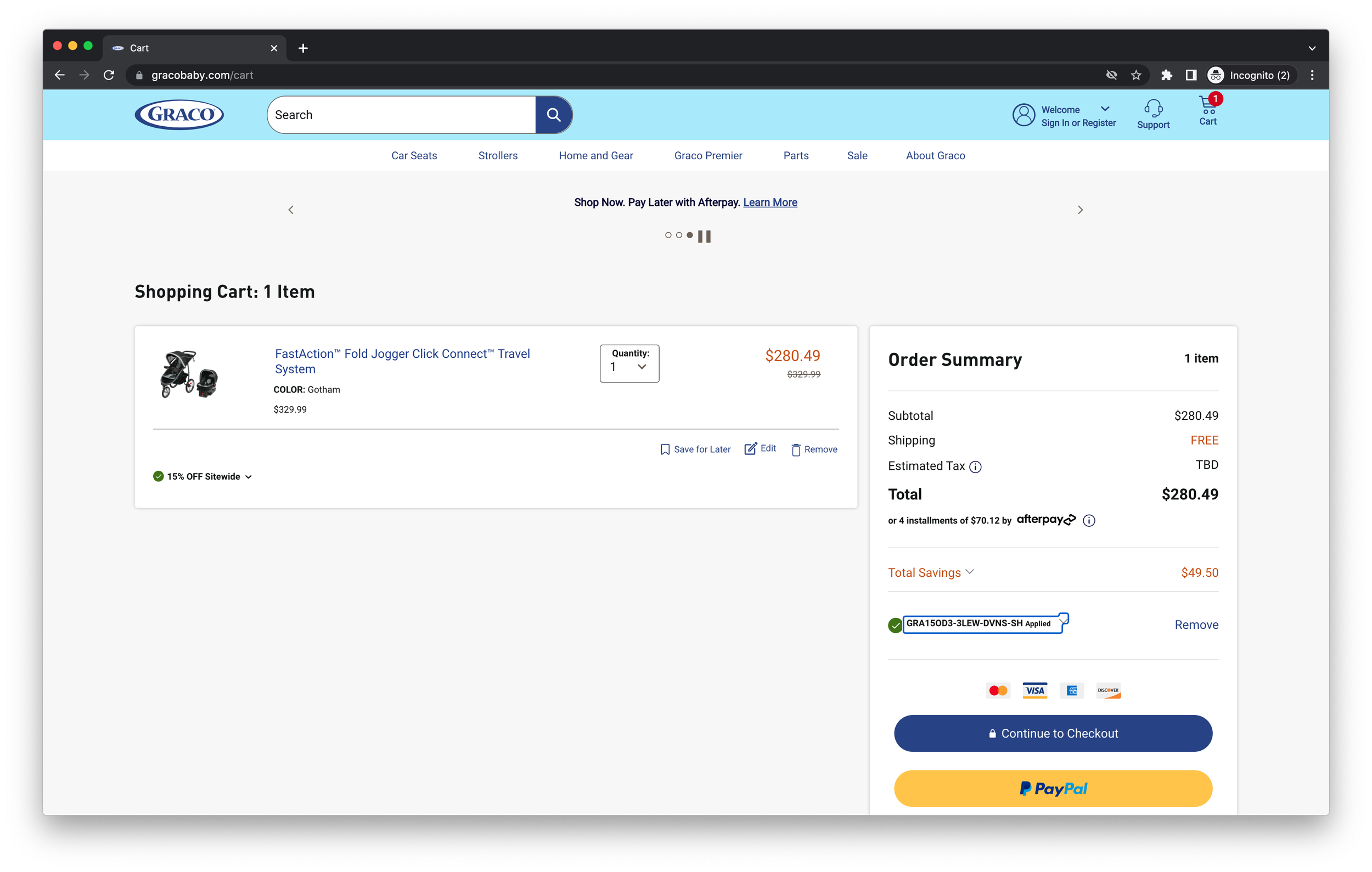
Next, we can go ahead and set up a few of these automations at random on some major retailer sites to do a bit of comparative analysis on (a) how often we generate the codes successfully, (b) how much money is spent in generating them, and (c) once we have the promo codes in hand, assert whether or not they can be redeemed by anybody who has simple possession of them (i.e. the attacker can generate them, and then provide them to anyone who wants to redeem them anonymously later). In the case of identifying the minimum viable abuse (MVA), we determined that proxy networks were likely a necessary component - in just the Graco Baby example, we were immediately hit with an attempt to block the traffic using CloudFlare - of course, being a coarse instrument of bot mitigation, it’s nearly useless when an IP without a pre-flagged reputation visits.
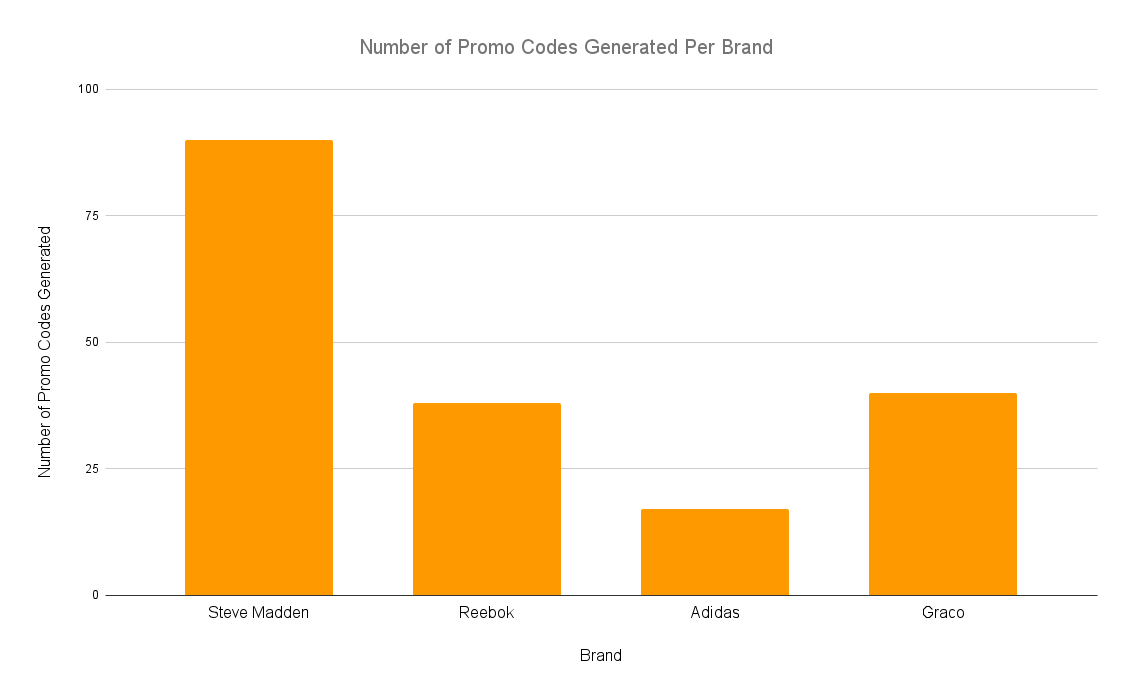
In our tests, we generated automations for Steve Madden, Graco Baby, Adidas, and Reebok. In total, we ran 395 automation tests against these retailers to determine if we could automate promo code generation. From that, we derived the average expected (bootstrapped) price per generation attempt to be $0.0668.
Average cost per signup attempt: $0.0668
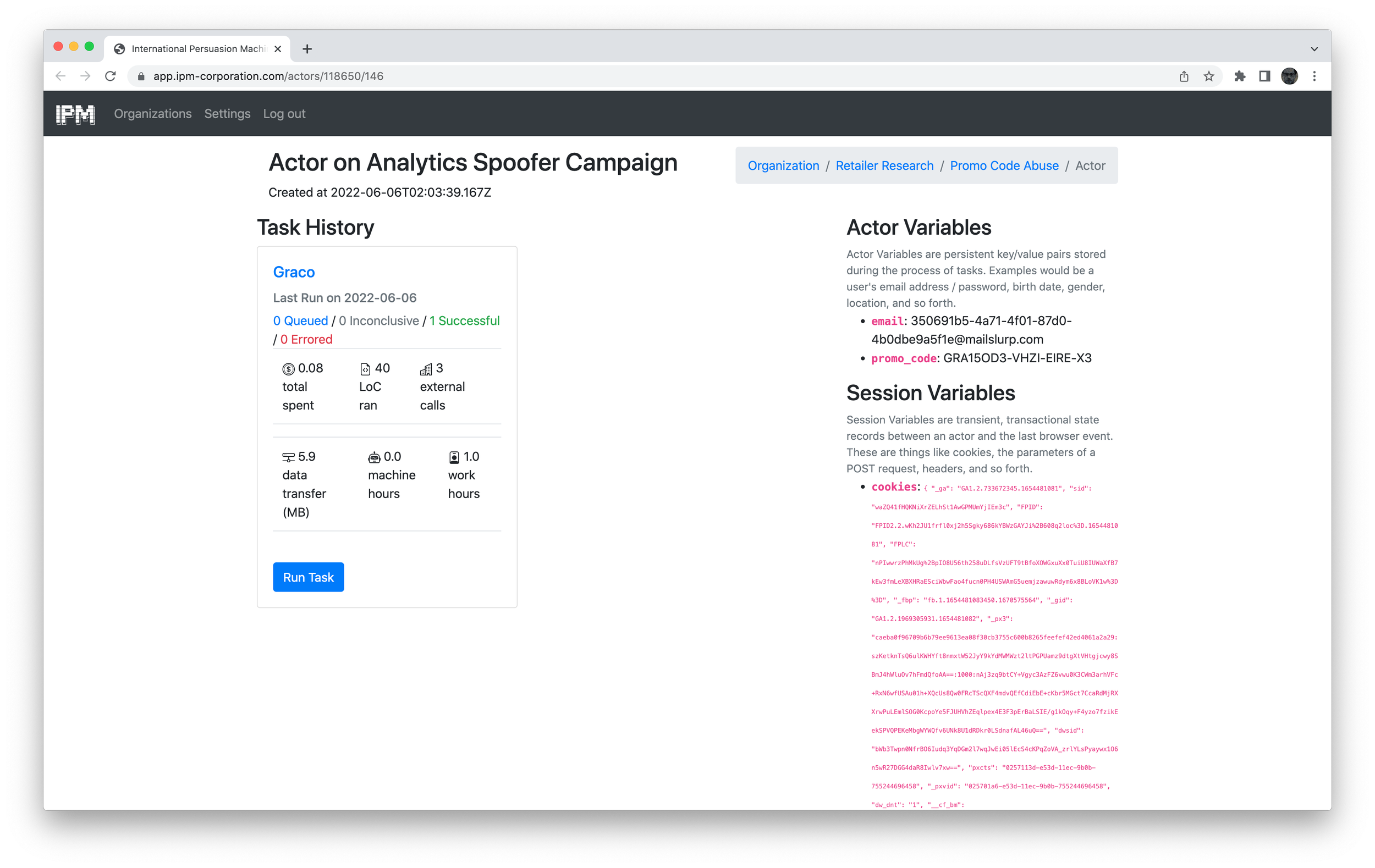
Once we generated the requests to receive these coupons, we then programmatically selected them from our emails with the IPM Vulnerability Engine, and stored them to each bot that attempted to receive them. We then looked at how many bots were successful versus how many failed. In many cases, the failures were simple reasons like the email was already in use (since we shared emails rather than provisioned a new one each time), or there were basic page state issues like trying to enter an email when the overlay didn’t automatically pop up on the page on load. In practice, individual bot makers targeting these systems directly would likely have a much higher success rate that, in the long limit, would approach a theoretically ideal cost around $0.0668 per promo code.
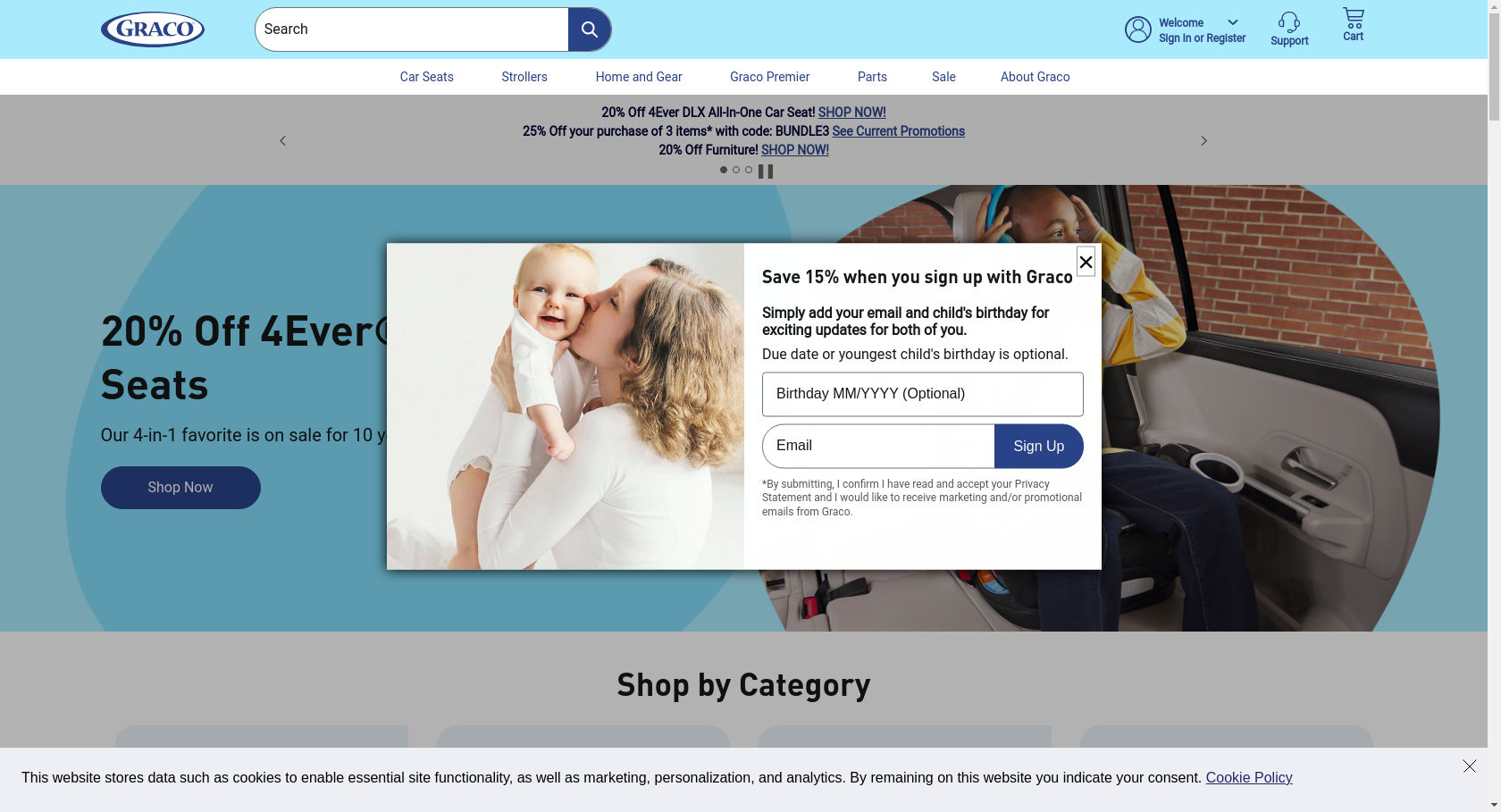
Adidas dutifully telling us that we were successful and providing our promo code
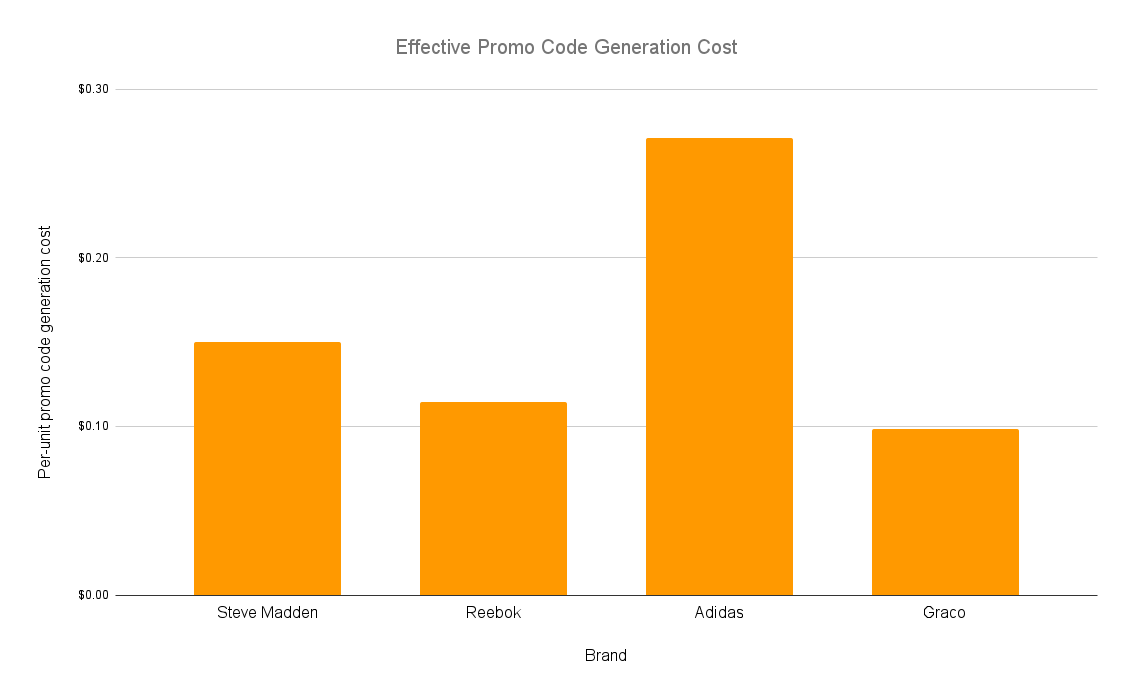
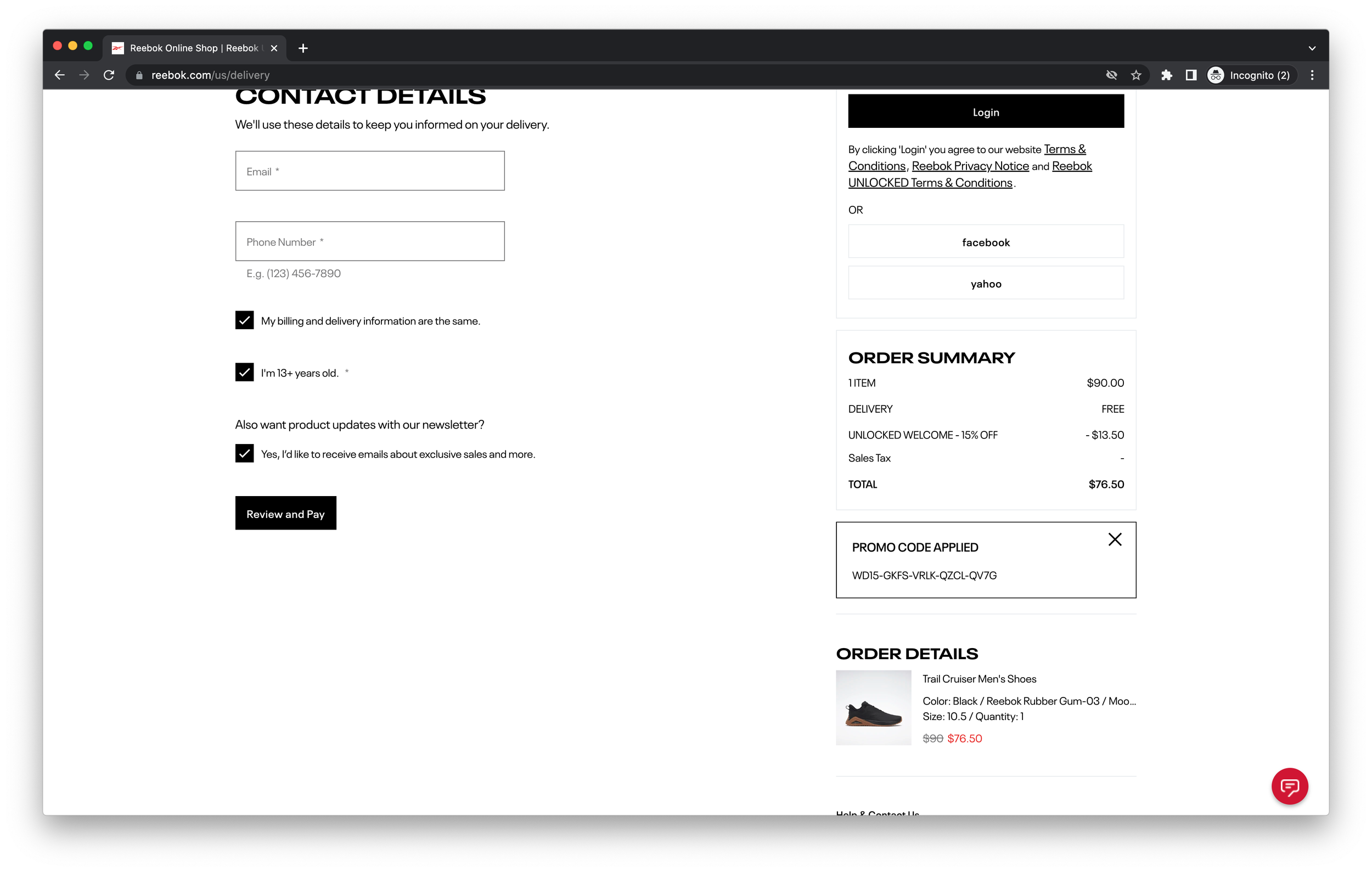
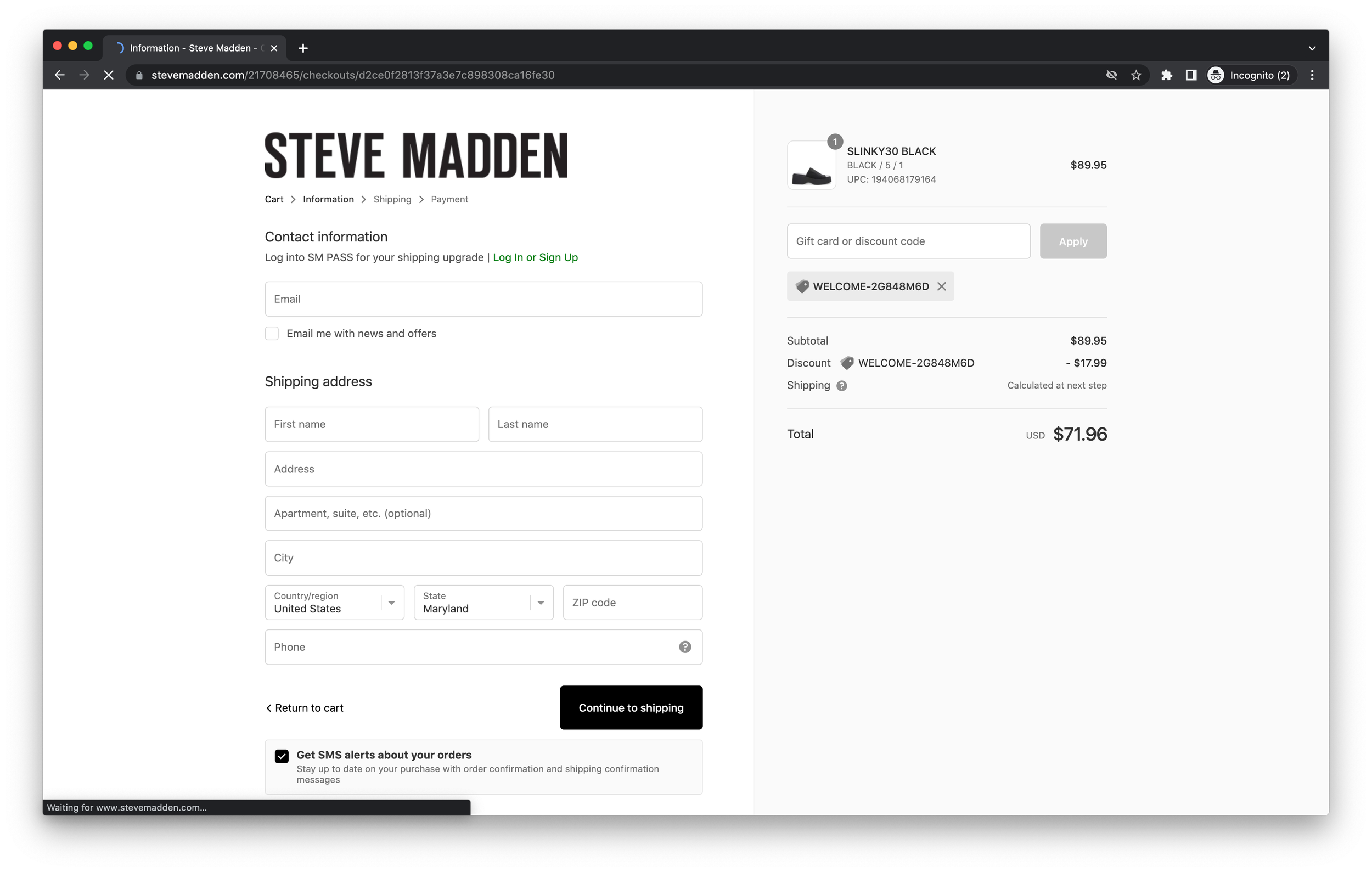
In each of these cases, we were able to prove that we could programmatically generate promo codes. We were able to generate 90 out of 202 for Steve Madden, 40 out of 59 for Graco Baby, 17 out of 69 for Adidas, and 38 out of 65 for Reebok. At an average per-automation cost of $0.0668, these resulted in costs of $0.149 for generating Steve Madden coupons, $0.098 for Graco, $0.271 for Adidas, and $0.114 for Reebok. Assuming a small purchase of $40, these would correspond to discounts of $8 on Steve Madden (98% net gain), $6 on Graco (98% net gain), $6 on Adidas (95% net gain), and $6 on Reebok (98% net gain). On larger purchases, the cost of the initial investment on mining promo codes decreases even further.

Ultimately, we found that Steve Madden, Graco Baby, Adidas, and Reebok all allowed us to redeem these promo codes when using anonymous shopping carts. In theory, that provides sufficient evidence that our attack would indeed work and scale to the level of a mechanized abuse operation - on various forums and gray-market reseller networks, we could provide these coupons. In fact, the more enterprising practitioner could in theory set up a site with a list of brands that you could click on, and generate promo codes on demand - while there are certain terms of service violations that may occur, again, nothing technically has been circumvented. Of course, it would be important for the practitioner to honor a cease and desist, but given how these retailers have set up their online marketplaces, there’s nothing that would prevent this from flourishing today.
IPM does not condone this type of behavior - instead, IPM seeks to help companies identify these problems early and stop them before they become issues. In each of these cases, we attempted to reach out to these retailers prior to publishing the work. We will again reach out - only time will tell if retailers wake up to these types of systemic issues, however. Until then, the $300 million to $600 million dollar illegal industry of promo code theft will keep growing unchecked, and will likely target the exact strategies we’ve identified.