Exploiting Lax Form Validation For Infinite Panera Brownies
One of the most basic recommendations IPM makes to our clients is to make the cost of an exploit less than the value of an exploit to would-be attackers.
While lots of other firms focus on post-hoc identification of attackers after an event, we encourage proactive work to understand the incentive structures inherent with technical affordances, and to engineer those incentives to align with the incentives of the organization.
What follows is an experiment wherein we prove that when organizations don’t follow this recommendation, sometimes it’s possible to get infinite brownies for free.
While we typically focus on entirely digital sociotechnical security, we set ourselves a challenge to identify a sociotechnical security flaw out in physical space that is mediated through digital platforms.
After some brainstorming, we decided to look for vulnerabilities in online food ordering systems. As these systems have exploded over the past decade, increasingly so during the COVID-19 pandemic, we surmise that they present a fairly large attack surface worth considering.
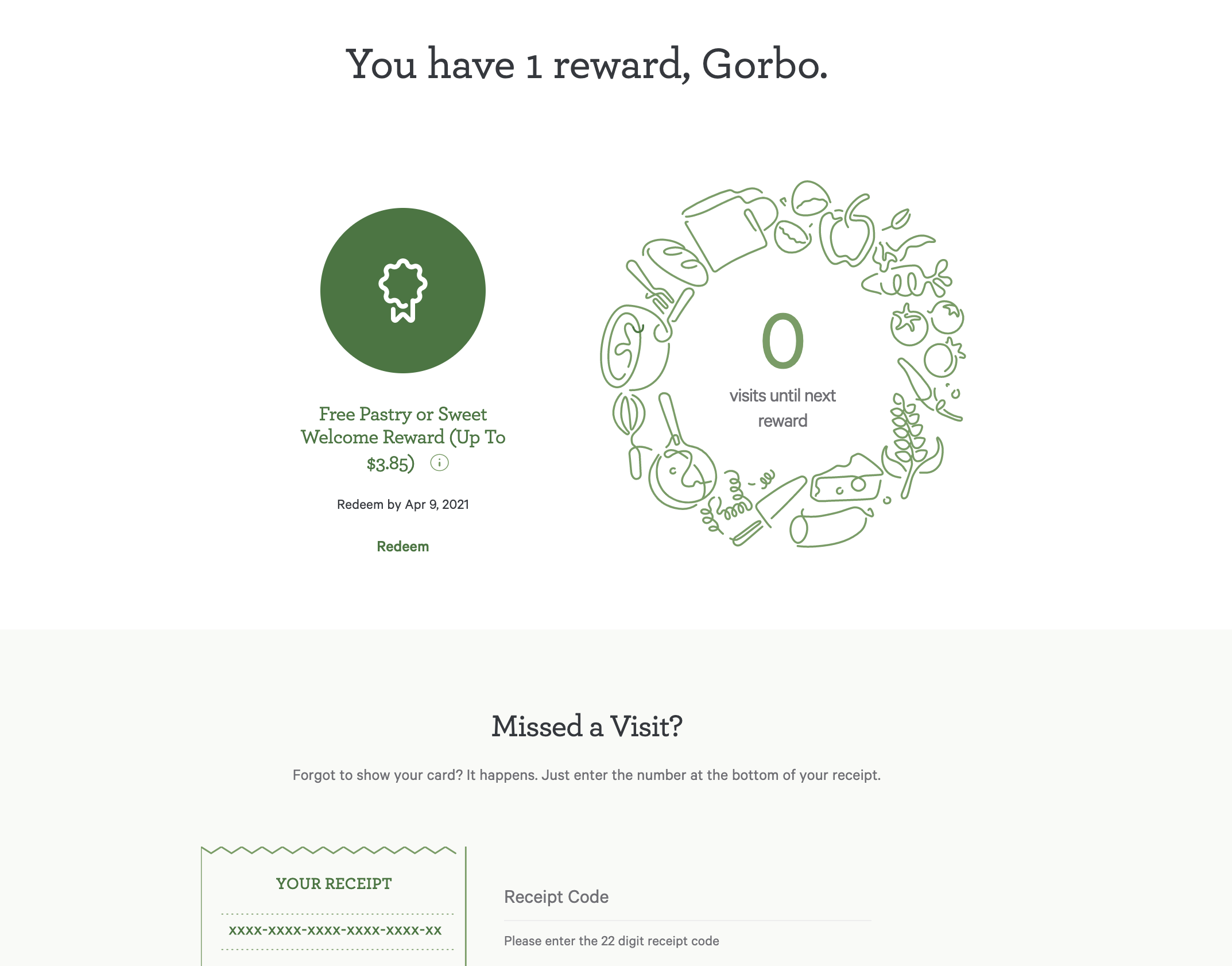
We narrowed our focus to rewards programs. After a bit of exploration, we identified a fairly clear security flaw in Panera’s MyPanera rewards program - when users sign up for the rewards program, they are provided with a free coupon for a pastry up to a value of $3.85. This coupon can be immediately used through the online ordering flow, which in turn, does not require credit card confirmation. The signup process itself is straightforward and only requires a few basic fields, none of which are required to be post-validated (e.g. no confirmation codes sent to email or phone number).
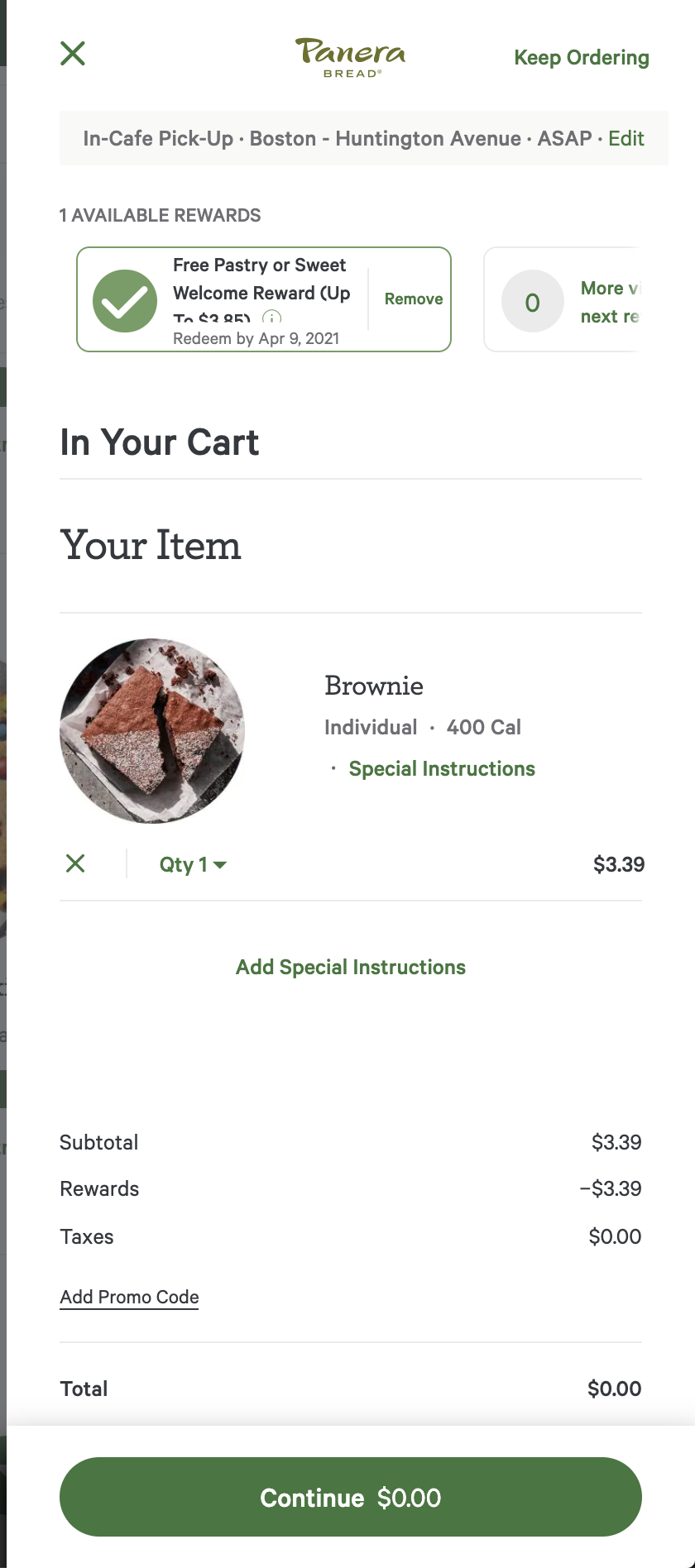
The signup itself is a discrete series of simple steps that can be conducted on any IP address. The estimated cost for a signup is around ≈$0.01. After signup, users have to navigate through the ordering process which requires entering an address, selecting a local store, selecting a pastry, and then applying the coupon.
While we did not automate this particular test, we can confirm that the IPM Vulnerability Engine estimates the full cost of this process to be in the region of ≈$0.08. For a $3.85 value, the incentives are aligned such that a technically-inclined person could easily automate this attack such that at the same time every day, a pastry is provided at a local Panera for their pickup.
With a bit more work, this type of attack could be generalized and deployed as a website microservice, for example, where anonymous users request infinite brownies by submitting (a) their local store, (b) the pastry of choice, and (c) the schedule on which they would like pastries to appear.
While unlikely, this type of scenario is entirely technically possible and requires surprisingly little automation - we estimate that a developer would likely have to research and ultimately deploy somewhere on the order of 100 lines of code in order to generate infinite brownies. As a proof of concept, we attempted a pickup of three pastries - first, we picked up a single pastry with a fresh throwaway MyPanera rewards account.
When this was successful, we determined to prove that “infinite” brownies can be achieved through proof-by-induction - could two pastries be picked up simultaneously from two brand new, fresh throwaway accounts?
With two simultaneous pastries in hand, we deduced that very little stands in the way of the “infinite brownies” scheme. With around 20 automatable steps and 100 lines of code, new MyPanera accounts can be generated with non-confirmed email addresses and phone numbers.
Given that MyPanera does not immediately attach to a credit card with the application of the reward coupon received at signup, there is no way to tie identity back to the purchaser, or induce a limit to the rate at which this scheme is deployed. Implementing IP-based signup rate limits, Credit Card authentication rate limits, or confirmation of signup details all raise the cost of the scheme - potentially to a point where actors will not engage in it.
At the time of this writing however, this incentive structure is ripe for abuse. Given that this loophole was detected with only a cursory analysis of the first online ordering platform we investigated, we expect that this is not unique to Panera.